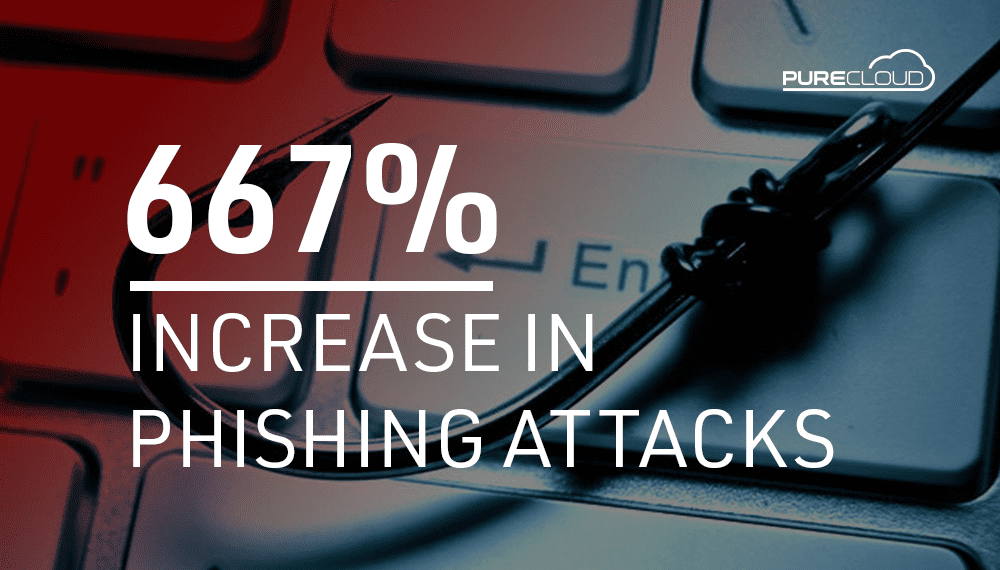
According to Barracuda networks since the outbreak of Covid-19, phishing attempts have soared dramatically by over 660%, as cyber criminals capitalise on the uncertainty of this global pandemic, and use it as a catalyst for their own gain.
This makes the fight against cyber crime even more difficult than before. And because phishing attacks are becoming more believable, utilising tactics that are increasingly hard to spot, beating the criminals can seem impossible.
But by getting inside the minds of the criminals behind these types of attacks, you could avoid becoming a victim and beat them at their own game. Gain insight into the motivation, techniques and targeting process involved in phishing attacks and how to make sure you are phish-savvy.
what’s their motivation?
When it comes to phishing attacks, the name of the game is always to make money. Criminals can do this in several ways. They can sell any personal data they obtain to other criminals to be used at a later date or they can access your funds directly and transfer money to their own bank accounts by stealing your login credentials. In some cases, if the criminal is unsuccessful in phishing you, you can be used as a pawn to phish someone else.
Phishing has become a lucrative method in recent years because the internet makes it very easy to move funds around without being caught. Plus, it allows the criminals to remain anonymous and avoid leaving a trail behind.
Phishing is cheap, easy and can be used to target a large number of people and unfortunately for us, money talks.
how do criminals create successful phishing attacks?
Phishing attacks are all about credibility. And the successful ones remove any barriers of doubt the victim may have about parting with their data. But while Dick Turpin used a handgun, modern-day criminals use technology, to appear as a trustworthy source.
Brand Impersonation
A lot of the time, criminals do this by posing as well-known brands and organisations that we tend to trust. They do this by purchasing widely available, low-cost phishing kits.
These kits deliver all the tools a phishing criminal would need to impersonate these brands by enabling them to copy the target site, configure a cloned site, capture victim information, and support their phishing efforts.
The Top 5 Impersonated Brands As Of February 2020 Were:
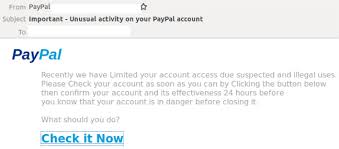
1. PayPal
2. Facebook
3. Microsoft
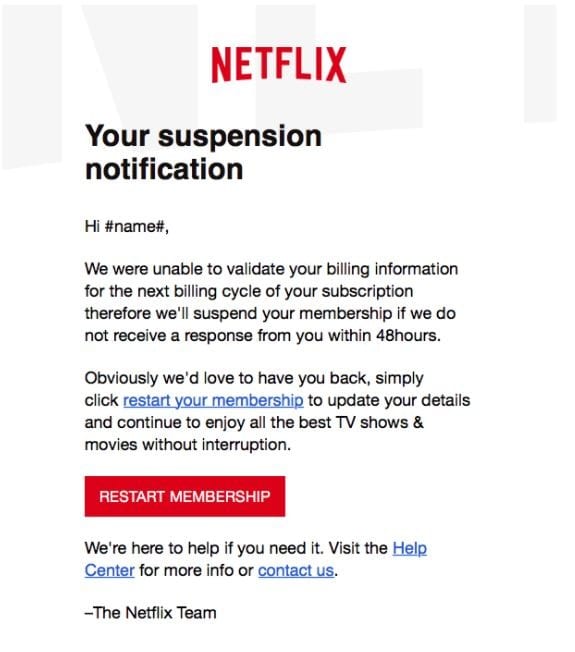
4. Netflix
5. WhatsApp
Phishing attacks like this are extremely simple to set up but incredibly hard to spot, as they often contain the brand logo, fonts, brand colours and more, all which lead you to believe it’s the real thing.
The scary thing about protecting against phishing attacks is they are constantly evolving. As soon as one type of phishing method is thwarted, it’s replaced with another that uses a different approach. Attackers are sophisticated and continue to look for new ways to get what they want.
targetting of victims
The truth is, when it comes to phishing, everyone is a target. Phishing itself has many different variants and these have evolved over time as the criminals get better. As in the real world of fishing, in cyber security, the name attributed to the phishing attack, can often indicate the effort required for the reward.
Email Phishing
This is just a generic email that’s sent to lots of people. It’s a very lazy type of phishing attack, but this is a numbers game. It’s a bit like throwing a net out there and praying you catch something.
Although it’s not a very sophisticated approach, it’s quick and even if only captures a few victims, it could easily net the perpetrators a good return on investment.
Spear Phishing
There’s a bit more effort required here. This approach typically focuses on a specific individual or organisation and is about adding something to the attack that is unique to the victim, so it appears more legitimate.
The cyber criminals will often turn to social media and company websites to research their victims. Once they have a better understanding of their target, they strike.
This technique is a lot like real spearfishing: there’s a bit more effort involved, but you tend to get the fish you want.
Whaling
There is a significant amount of effort involved in whaling. These attacks attempt to steal sensitive information and often targets high calibre victims such as those in senior management.
Whaling emails are more sophisticated and harder to spot than most phishing attacks. That’s because they have been crafted using extensive research on individuals and will often use a more believable corporate tone.
These phishing attacks have a high return for the cyber criminals. Much like whaling in the real world, if just one of these pays off, it can feed the family for a whole year.
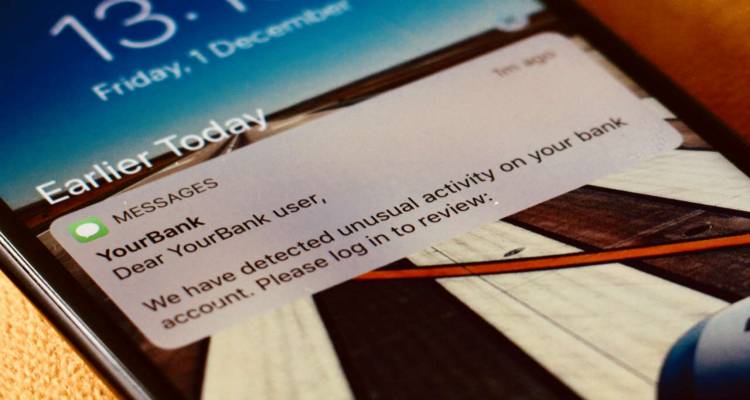
Smishing and Vishing
These are often used in combination with other attacks and replace emails with a text message or a voice call.
They typically aim to gain the victim’s trust and force them to act quickly to gain sensitive information such as login details, passwords, and pin.
I like to think of these as the fishing rod and bait. They can be very successful when used together.
Angler Phishing
Imagine this as the fishing trip before going whaling as a means of obtaining bait. Criminals use this type of attack to gain information that will make their next attack work better.
The type of bait received at this point determines the next method of attack. Angler phishing is being used more frequently by attacks utilising fake social media profiles.
The Fear Factor
In a lot of these cases, phishing criminals will use scare tactics, such as something being time sensitive, or spoof emails from superiors to force an emotional snap decision, to increase the successfulness of their attack.
Tapping into people’s fears to this extent, often means that victims are so scared, they can’t spot the signs of bogus emails. And that’s exactly what the criminals want.
HOw phishing attacks are sent
As with any criminal venture, timing is critical when sending phishing attacks. That’s because the best phishing attacks really are “right place, right time”.
Cyber criminals spend a long time researching victims and monitoring their behaviour so they can increase their chances of success. They do this by catching us off guard and sending scams at times when we are vulnerable, or least likely to be busy.
Take the recent Covid-19 events as an example. This has been a hot topic on everyone’s lips for the last few months, with people constantly looking for guidance, support, advice, or updates from reputable sources.
The pandemic became a phishing attacker’s dream. And the cyber criminals jumped at the chance to flood inboxes with relevant phishing attacks.
Top Covid-19 phishing subject lines were:
Password Check Required Immediately | CDC Health Alert Network: Coronavirus Outbreak Cases | PTO Policy Changes
Scheduled Server Maintenance – No Internet Access | Test of the [[company_name]] Emergency Notification System
You have been added to a team in Microsoft Teams | List of Rescheduled Meetings Due to COVID-19
SharePoint: Coronavirus (COVID-19) Tax Cut Document| Confidential Information on COVID-19 | IT: Work from home – VPN connections
So while technology has helped us to support the coronavirus effort, it’s also helped to wreak havoc with phishing attacks.
HOw to avoid being phished
With 3.4 billion malicious emails sent every day, phishing is very much alive and kicking. Even if you have the most sophisticated technology in place to protect your business, it’s almost inadequate when it comes to phishing, because these attacks don’t doesn’t target technological weaknesses. Instead they go after your employees.
To avoid being a victim of phishing you need to know how to spot the attacks and take simple measures to protect yourself.
Spotting Phishing Attacks
A Mismatched URL
The Email Requests Personal Information
Legitimate companies do not email to ask for sensitive information like passwords or account numbers.
Poor Spelling & Grammar
Reputable company emails to customers, are often proof read to ensure flawless spelling and grammar. If there’s spelling mistakes, you might be being phished.
Urgency & Fear
Be cautious of emails that urge you to do something that you feel is rushed or wrong and always double check authenticity.
protecting yourself
Educate Staff
Phishing attempts require humans to work. Use a platform like Cybsafe to educate staff on what they should be looking out for and how to report suspicious emails.
Never Click on Suspicious Links
The criminals need you to do this for their attack to work, so always be suspicious and never let yourself feel pressured into clicking a link in an email.
Install & Update Technology
Technology is crucial in detecting threats on your computer and blocking unauthorised users from gaining access. Make sure it’s always updated to prevent vulnerabilities.
Passwords and 2FA
Never use the same password for more than one site and turn on two-factor authentication (2FA) if you can as this is a real deterrent for phishing criminals.
stay alert
Criminals are seeking to exploit our greater use of emails, video conferencing and other technologies for their advantage and we all have a part to play in making sure they don’t succeed.
Make sure you stay alert and remain vigilant when browsing your emails and never give your details away without consideration of who is asking for them. If you spot what you believe to be a fraudulent phishing email, you can now report this to the National Centre for Cyber Security and help protect others too.
DON’T TAKE THE BAIT
Phishing attacks are a real threat to every business and if you’re not clued up, you could get caught out. And the impact could be devastating. Get in touch with the cyber experts at PCS for more advice and support on how to protect your business from phishing attacks. Call us on 0333 150 6780, email or fill out the contact form below and a member of the team will be in touch.









Recent Comments