According to recent research, cyber criminals launch one cyber-attack every 39 seconds! They do this using a range of attacks, but over the last few months, there’s been a huge increase in Spoofing attacks. This technique allows criminals to gain access to data, information, and networks easily and without being detected.
In fact, Microsoft estimates that attackers behind spoofing are able to remain undetected on a network for roughly 146 days. This gives the cybercriminals plenty of time to extract the information or data they want and wreak havoc within your business.
The trouble with spoofing attacks is that it comes in so many different variations and they’re getting more sophisticated.
And while technology as a defence is a good start, spoofing attacks generally creep through the cracks, relying on the art of deception to fool their targets – your users.
Mimecast found that 84% of businesses are concerned about being caught out by spoofing attacks. And rightly so – no one is safe. On average, companies receive 9 spoofing attacks per year.
WHAT IS A SPOOFING ATTACK?
Spoofing is a technique used by cybercriminals to trick end users and business networks into believing they are someone or something they’re not. Criminals disguise themselves as an authentic source, usually someone that is known and trusted by the victim.
In some cases, cybercriminals will personalise these messages to add credibility and convince the victim that they are having legitimate interactions. Most of the time though, simply disguising themselves as a big brand name, organisation, supplier or senior employee is motivation enough to part with personal information, click links or open attachments.
This impersonation tactic is used in around 68% of all phishing attacks where criminals use known and trusted brands or individuals as their display names to fool targets into participating in, unbeknownst to them, malicious and criminal activity.
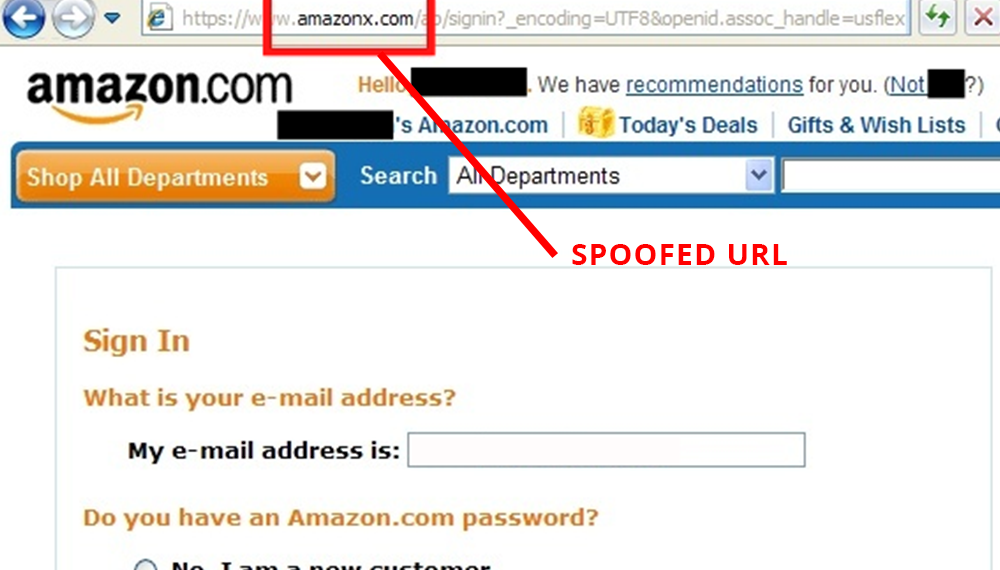
A good example of a spoofing attack in action is receiving an email from Amazon asking to confirm purchases. You never made the purchases so click the link to verify and are sent to, what looks like, the Amazon website. You enter your details and before you know it, you’ve been spoofed.
Because instead of visiting Amazon, you’ve clicked a malicious link that’s sent you to a spoofed URL using the same brand colours and logo to create a fake login page. Whilst legitimate on the surface, your details have just been harvested for sale on the dark web or for use in a future cyber-attack.
For businesses, a successful spoofing attack is extremely serious and can be the groundwork for other, more serious attacks.
Once duped, businesses could be targeted with ransomware, tricked into parting with funds or experience a data breach, which has financial and reputational implications.
DID YOU KNOW?
There are many different types of spoofing attacks, but the main ones that cybercriminals use with the most success are IP spoofing, email spoofing and caller ID spoofing.
Click here to out more about these and other spoofing attacks that target SMB’s.
SPOOFING & SOCIAL ENGINEERING
Now you know what spoofing attacks are, let’s look at how they work. It doesn’t matter what the spoof is, there is always an extensive research phase completed by the criminal to make their attack appear legitimate.
This usually involves social engineering.
Social engineering is a common method used by cybercriminals use to trick victims into doing what they want. Be it giving up personal information, clicking malicious links, or opening infected attachments. It involves 4 stages: planning, research, contact and execution. Ultimately though, it is a technique reliant on human vulnerability.
Human vulnerabilities aren’t always bad. But often, cybercriminals tend to exploit emotions such as fear, naivety, curiosity, empathy, greed, and vanity, to convince us to do something we wouldn’t normally do.
HIDING THEIR IDENTITY
There are many ways cyber criminals hide their identity. A tried and tested method used by hackers is to target unsecure mail servers. This enables them to complete the most common form of spoofing – email spoofing.
Amateur hackers will use a random address in the “From” field of emails. The only problem in doing this is if the victim replies the response will go to whoever is listed in the “From” field—not the attacker, and they will be rumbled. This technique is normally used to bypass spam filters and avoid detection because the attackers are using a legitimate “From” email address.
Another way cybercriminals spoof emails is by using a domain name similar to the one they’re trying to spoof. For example, “rn1crosoft.com”. Note the use of the number “1” instead of the letter “i”. The attackers also use “r” and “n” to give the illusion of the letter “m”. This also gives the attacker a domain to assist in the creation of a spoofed website to add even more credibility.
This is just one example, but you can see how easy it is for attackers to pretend to be someone, or something they’re not and easily fool their targets.
TELL-TALE SIGNS OF website spoofing
No Lock Symbol
All reputable websites have an SSL certificate, which means a third-party has verified the web address belongs to the organisation.
HTTP vs HTTPS
Legitimate websites will almost always use HTTPS, the encrypted version of HTTP, when transferring data back and forth. If you’re on a login page and you see “http” as opposed to “https” be suspicious.
Password Managers
A password manager helps you to keep secure passwords and will autofill your login credentials for any legitimate website you save in your password vault. If you navigate to a spoofed website your password manager will not fill in the username and password fields for you—a good sign you’re being spoofed.
TELL-TALE SIGNS OF email spoofing
Mismatch Sender & Email
Double check the sender’s address. As mentioned, scammers will register fake domains that look very similar to legitimate ones.
URL’s & Attachments
Be wary of attachments and links in emails received from an unknown sender. If in doubt always air on the side of caution. Never open attachments and check URLs before clicking by hovering over them with your cursor to see if it’s legitimate.
Mistakes
Scammers don’t proofread their work, even though they put a lot of time and effort into it. Typos, bad grammar, and unusual syntax are usually a sign that emails are not legitimate.
TRAIN STAFF – PROTECT YOUR BUSINESS
According to a study by Mimecast called the State of Email Security, 55% of organisations do not provide regular awareness training for their staff. They instead are solely reliant on internal and external cybersecurity measures to protect them from the risk of spoofing attacks.
Yet while these help reduce the risk of attacks reaching your end-users, they can do nothing to protect you if a spoofing attack reaches your staff. In fact, research proves that secure email gateways (SEGs) fail to stop around 99.5% of all email spoofing attacks.
That’s why it’s incredibly important to give yourself a lifeline when it comes to your cyber security defence by training those likely to be targeted – your staff!
But with the right security awareness training program you can make them a crucial element in the fight against cybercrime.
Nobody is safe from spoofing attacks, but with the right training and equipment, you can bolster your defences and keep the cyber criminals at bay.









Recent Comments